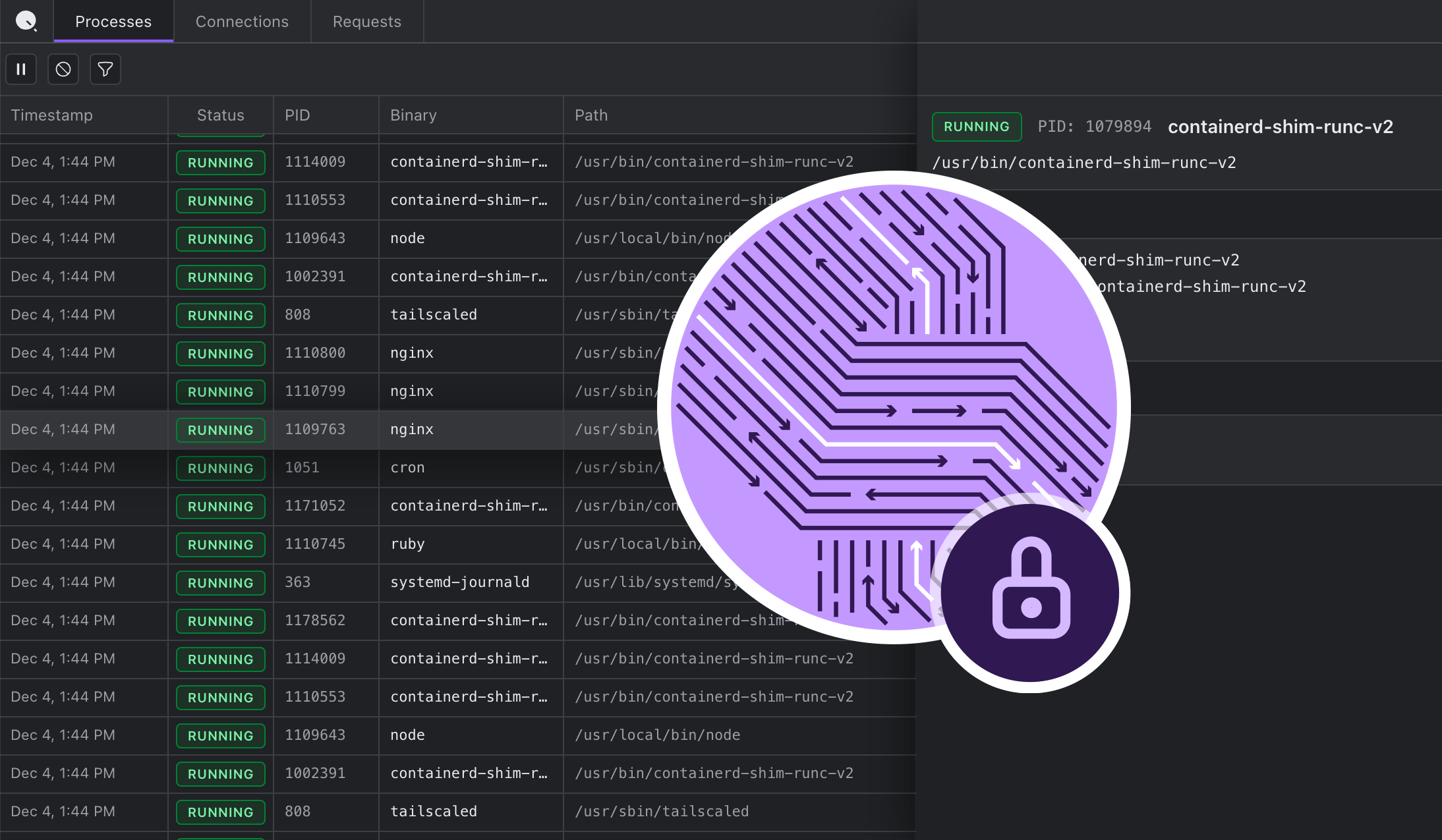
Introducing DevTools: Chrome-style Network Tab for Your Linux Server
We built a browser-based debugging tool that shows live http/s traffic on production servers. No proxies, no certificates, no code changes. Just the visibility we always wished we had. 

Tyler Flint
December 4, 2025

The Heisenberg Horror: Why Debugging Tools Make Bugs Disappear
Production bugs that vanish when you try to debug them. Learn why traditional debugging tools change what they observe and how to catch Heisenbugs with unmatched visibility.

Devin Bernosky
November 25, 2025
Built to Integrate: Why Qpoint's Modular Architecture Matters
Most security vendors force you into all-or-nothing adoption. Learn why Qpoint's modular architecture (QTap, QPlane, QScan) gives you unmatched visibility with complete flexibility over data storage, deployment, and integration.

Devin Bernosky
November 14, 2025
The CISO's Checklist - What Your Current Tools Can't Tell You
As a CISO, you've invested heavily in security tools. Yet when the board asks about your organization's true risk exposure, you still face uncomfortable silence around critical questions. The problem lies in what encryption hides from your existing security stack.

Devin Bernosky
October 30, 2025
Are You Watching What's Leaving Your Network?

Devin Bernosky
November 5, 2025
The Hidden Complexity of External Dependencies - How Qpoint Solves a Cloud-scale Problem

Jon Friesen
November 4, 2025
The M&A Due Diligence Black Box: Why Technical DD Takes Weeks (And How to Get It Done in Days)

Devin Bernosky
October 28, 2025
How eBPF-Based Egress Monitoring Would Have Caught the Shai-Hulud npm Worm in Real-Time

Devin Bernosky
September 26, 2025

The Encryption Paradox

Devin Bernosky
September 9, 2025

Why Running Qtap in Production is Safe - A Deep Dive into eBPF and Privilege Boundaries

Jon Friesen
September 5, 2025
The eBPF Verifier - How Linux Safely Runs User Code in Kernel Space

Jon Friesen
September 2, 2025

The Impossible Proxy - An Egress Journey

Devin Bernosky
September 2, 2025
Security Observability for the Encrypted Cloud

Tyler Flint
April 29, 2025

A Story About Missing Context

Devin Bernosky
April 15, 2025

Qpoint Achieves SOC 2 Type II Compliance

Jon Friesen
March 18, 2025
The Truth is on the Wire

Rob Genova
February 4, 2025